Authorizing AWS CloudFormation Role to perform iam:CreateRole on Resources
Learn how to enable CloudFormation to create roles for your AWS resources.
CodePipeline Error Message
When I added a policy statement to enable my lambda to use AWS Polly synthesize speech API, CodePipeline ExecuteChangeSet failed with a CloudFormation IAM role error.
My Lambda function declaration in yaml:
Type: 'AWS::Serverless::Function'
Properties:
Handler: helloWorld.handler
Runtime: python3.6
MemorySize: 128
Description: 'helloWorld'
FunctionName: helloWorld
Policies:
- Statement:
- Effect: "Allow"
Action:
- "polly:SynthesizeSpeech"
Resource:
- "Fn::Sub": "arn:aws:polly:${AWS::Region}: \
${AWS::AccountId}:lexicon/*"
The following is the error message I saw on CodePipeline console. Note that test was my project name and thus the message contains ‘CodeStarWorker-test’.
CodeStarWorker-test-CloudFormation/AWSCloudFormation is not
authorized to perform: iam:CreateRole on resource:
arn:aws:iam::AccountId:role/
awscodestar-test-lambda-helloWorldRole-V5QUHYDCDRBA
Solution
Follow the steps below to add IAM policies to your CloudFormation role that are needed to execute role creation for other resources.
- Go to AWS IAM console and select Role on the left panel.
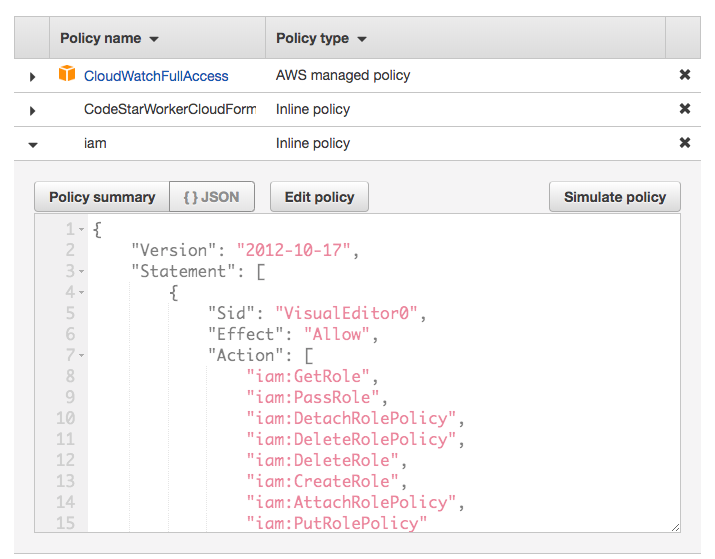
- Look for your project CloudFormation role by typing in your project name. Your CloudFormation role summary will look like the screenshot below.
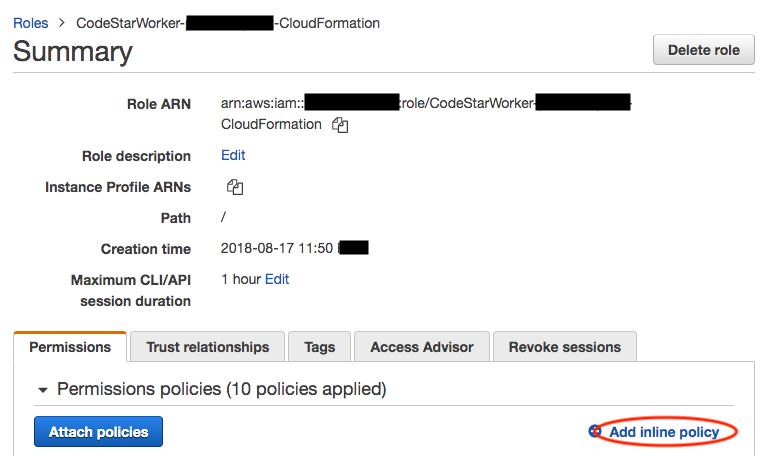
- Click on
Add inline policybutton to open up policy editor and selectJSONtab when it is opened.
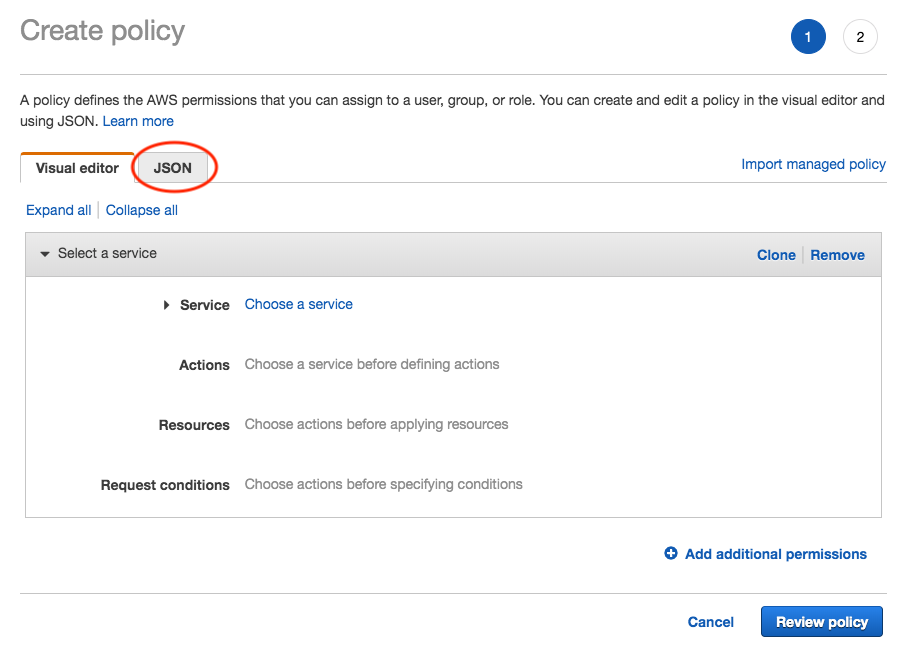
- Paste in the following JSON object into the input field. You may not need all, thus, you can experiment by adding
iam:CreateRolefirst and add other actions when they are needed.
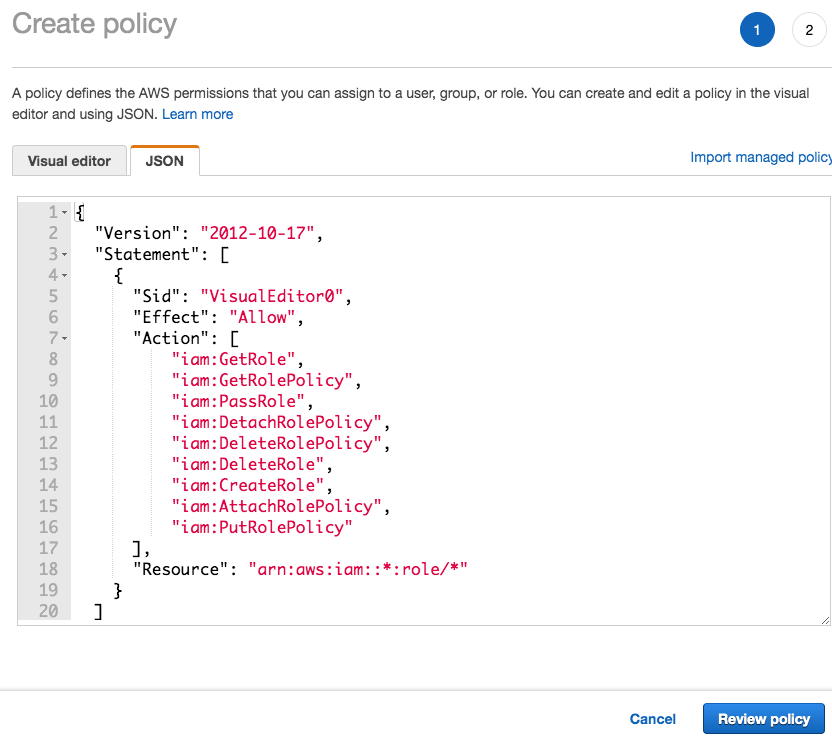
AWS IAM policy statement with allowed IAM actions.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:GetRolePolicy",
"iam:PassRole",
"iam:DetachRolePolicy",
"iam:DeleteRolePolicy",
"iam:DeleteRole",
"iam:CreateRole",
"iam:AttachRolePolicy",
"iam:PutRolePolicy"
],
"Resource": "arn:aws:iam::*:role/*"
}
]
}
- Then, review and give the inline policies item a name to complete the addition of policies.
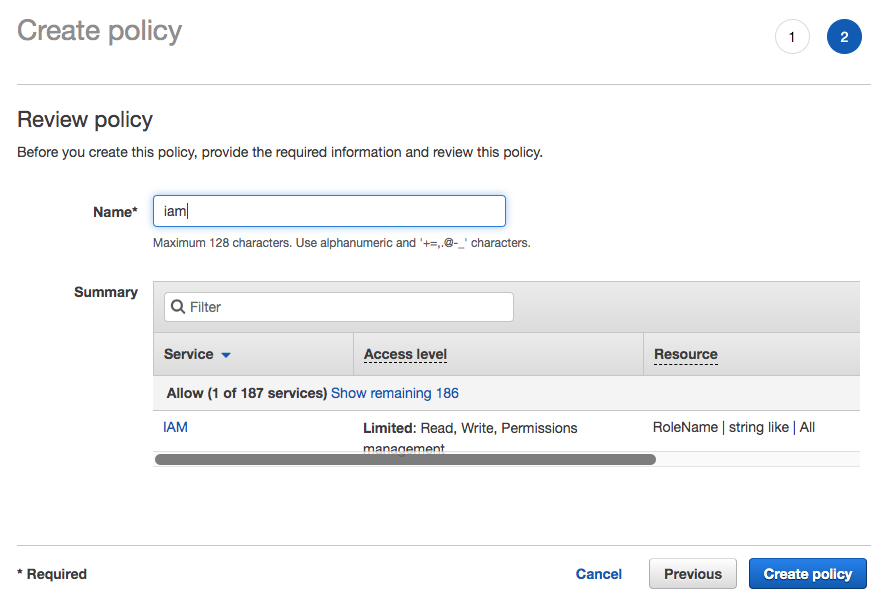
- Now, necessary IAM policies have been added to your CloudFormation role. You can make some changes to your code or yaml and push to trigger rebuild.
Summary
With addition of necessary IAM policies, CloudFormation will be able to create roles successfully for your resources. If there are other similar IAM errors, you can fix by adding necessary roles by reading the error message carefully.
Support Jun
Thank you for reading! 
If you are preparing for Software Engineer interviews, I suggest Elements of Programming Interviews in Java for algorithm practice. Good luck!
You can also support me by following me on Medium or Twitter.
Feel free to contact me if you have any questions.



Comments